Hello Everyone,
We're glad to announce that ModSecurity is now officially enabled on our VPSs!
Here is more information regarding the matter as taken from our blog:
ResellersPanel.com Blog
"ModSecurity now enabled with all VPSs
The ModSecurity Apache module is a great solution forminimizing the number of hack attacks to websites and applications.
It acts as an application-layer firewall and is able to effectively prevent most brute force/ URL forgery attacks and forum spamming attempts targeted at sites.
Some time ago, we enabled the ModSecurity protection layer as a default feature with all shared hosting accounts. Now the highly effective anti-hack firewall is enabled with all VPSs as well.
ModSecurity enabled on all VPSs
As with shared hosting accounts, the ModSecurity firewall is enabled by default on your VPS, so you don’t have to configure anything in order to have your websites protected.
ModSecurity is running in a blocking mode, so it will automatically block all incoming requests that are flagged as insecure according to the commercial rules at http://www.atomicorp.com.
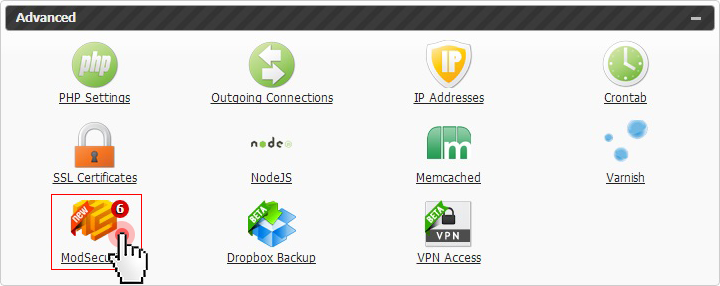
You can access the ModSecurity section in the Hepsia Control Panel from the newly added shortcut on the Control Panel’s home page or from the Advanced drop-down menu:
How does ModSecurity exactly work?
Over 70% of all the attacks are now carried out at the web application level and being a web application firewall (WAF) itself, ModSecurity effectively addresses this problem.
Its purpose is to establish an external security layer, which allows for HTTP traffic monitoring and real-time analysis, and it offers a powerful API for implementing the advanced protection needed.
This way, the firewall ensures an enhanced level of security, where the malicious attacks are detected and prevented before they reach the web applications.
ModSecurity against brute force attacks
ModSecurity has proven to be very efficient in preventing “brute force” attacks, i.e. the attempts to guess the username and the password of a web application, using a predefined set of
usernames and passwords and combining them randomly.
Thanks to the ModSecurity firewall, if there are more than 15 failed login attempts from an IP address within 3 minutes, the IP address will be blocked from accessing the website for the next 30 minutes.
So far, the ModSecurity plugin has reduced the number of hacked websites on our servers dramatically.
If you have any questions about ModSecurity and about how it will work on your Virtual Private Server, don’t hesitate to contact our support team by opening a ticket from the Web Hosting Control Panel."
Best Regards,
Ian Stone
We're glad to announce that ModSecurity is now officially enabled on our VPSs!
Here is more information regarding the matter as taken from our blog:
ResellersPanel.com Blog
"ModSecurity now enabled with all VPSs

The ModSecurity Apache module is a great solution forminimizing the number of hack attacks to websites and applications.
It acts as an application-layer firewall and is able to effectively prevent most brute force/ URL forgery attacks and forum spamming attempts targeted at sites.
Some time ago, we enabled the ModSecurity protection layer as a default feature with all shared hosting accounts. Now the highly effective anti-hack firewall is enabled with all VPSs as well.
ModSecurity enabled on all VPSs
As with shared hosting accounts, the ModSecurity firewall is enabled by default on your VPS, so you don’t have to configure anything in order to have your websites protected.
ModSecurity is running in a blocking mode, so it will automatically block all incoming requests that are flagged as insecure according to the commercial rules at http://www.atomicorp.com.
You can access the ModSecurity section in the Hepsia Control Panel from the newly added shortcut on the Control Panel’s home page or from the Advanced drop-down menu:

How does ModSecurity exactly work?
Over 70% of all the attacks are now carried out at the web application level and being a web application firewall (WAF) itself, ModSecurity effectively addresses this problem.
Its purpose is to establish an external security layer, which allows for HTTP traffic monitoring and real-time analysis, and it offers a powerful API for implementing the advanced protection needed.
This way, the firewall ensures an enhanced level of security, where the malicious attacks are detected and prevented before they reach the web applications.
ModSecurity against brute force attacks
ModSecurity has proven to be very efficient in preventing “brute force” attacks, i.e. the attempts to guess the username and the password of a web application, using a predefined set of
usernames and passwords and combining them randomly.
Thanks to the ModSecurity firewall, if there are more than 15 failed login attempts from an IP address within 3 minutes, the IP address will be blocked from accessing the website for the next 30 minutes.
So far, the ModSecurity plugin has reduced the number of hacked websites on our servers dramatically.
If you have any questions about ModSecurity and about how it will work on your Virtual Private Server, don’t hesitate to contact our support team by opening a ticket from the Web Hosting Control Panel."
Best Regards,
Ian Stone

Comment