Clive is usually the one who posts these along with the other admins, but I figured since I saw it, I might as well since it hasn't been posted here yet.
Brute-force prevention on the WordPress login page
The web has seen an increased frequency of brute force attacks on WordPress sites recently, with malicious bots making hundreds of requests to the servers and generating a great amount of load on WordPress-based sites.
To minimize the risk of unauthorized access to yours and your customers’ WordPress sites, our developers have added an extra level of security to the WordPress login page.
As of today, our system will block for a period of 30 minutes each IP address that generates more than 15 login attempts within 3 minutes.
This brute-force prevention functionality is now enabled by default for all WordPress-driven websites.
It is conveniently integrated into the ModSecurity firewall interface, so you can easily manage it.
Once an IP address has been blocked, you will see it highlighted in red in the Detected Attacks column on the ModSecurity information board: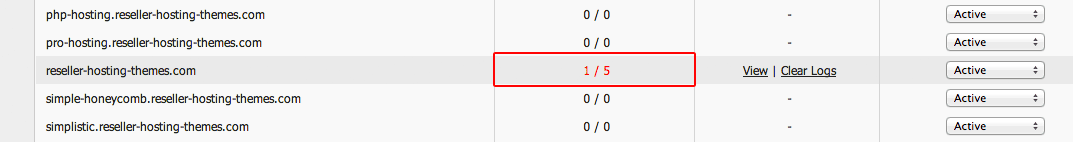 To see the log file for the blocked IP address, click on the ‘View’ link on the right:
To see the log file for the blocked IP address, click on the ‘View’ link on the right: 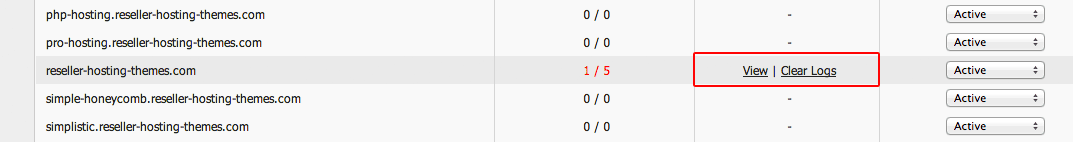 In the popup window, you will see a record of the blocked IP address, so you will know where the sequence of unauthorized login attempts originates from:
In the popup window, you will see a record of the blocked IP address, so you will know where the sequence of unauthorized login attempts originates from: 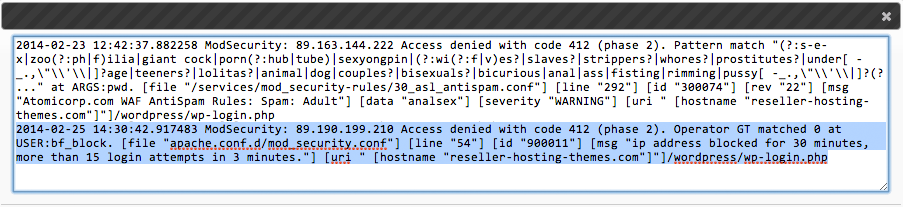 If, for some reason, you want to disable the brute-force prevention functionality for your WordPress site, you can do so in two ways: - by putting the ModSecurity firewall in Detect mode; This means our system will still generate a log file for the detected login attempts, but the IP address will not be blocked:
If, for some reason, you want to disable the brute-force prevention functionality for your WordPress site, you can do so in two ways: - by putting the ModSecurity firewall in Detect mode; This means our system will still generate a log file for the detected login attempts, but the IP address will not be blocked: 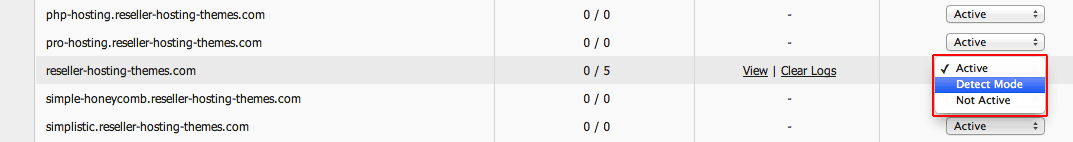 - by disabling ModSecurity completely:
- by disabling ModSecurity completely: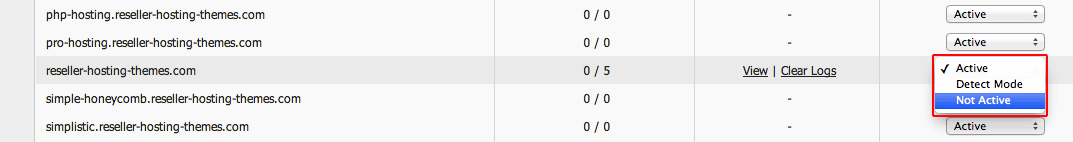
Hopefully, this newly added level of brute-force protection will help you maintain a more secure WordPress-based web presence.
Source: http://blog.resellerspanel.com/lates...ogin-page.html
Brute-force prevention on the WordPress login page
The web has seen an increased frequency of brute force attacks on WordPress sites recently, with malicious bots making hundreds of requests to the servers and generating a great amount of load on WordPress-based sites.
To minimize the risk of unauthorized access to yours and your customers’ WordPress sites, our developers have added an extra level of security to the WordPress login page.
As of today, our system will block for a period of 30 minutes each IP address that generates more than 15 login attempts within 3 minutes.
This brute-force prevention functionality is now enabled by default for all WordPress-driven websites.
It is conveniently integrated into the ModSecurity firewall interface, so you can easily manage it.
Once an IP address has been blocked, you will see it highlighted in red in the Detected Attacks column on the ModSecurity information board:


 If, for some reason, you want to disable the brute-force prevention functionality for your WordPress site, you can do so in two ways:
If, for some reason, you want to disable the brute-force prevention functionality for your WordPress site, you can do so in two ways:

Hopefully, this newly added level of brute-force protection will help you maintain a more secure WordPress-based web presence.
Source: http://blog.resellerspanel.com/lates...ogin-page.html

Comment